Single Sign-On - The problem
In the past, multi-user computers have always stored all user accounts locally,
even when these computers were part of a network.
fig. 1 Network with a central user database
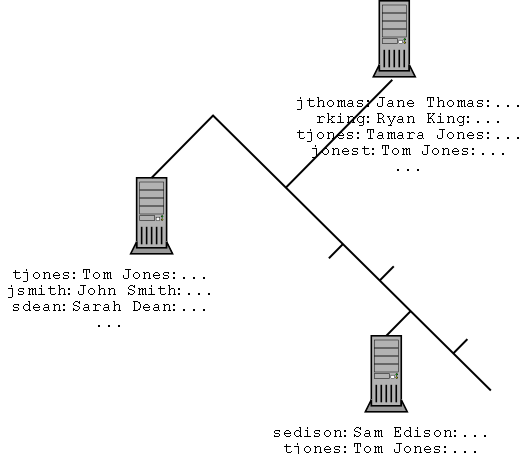
The user "Tom Jones" has a separate account for each computer. This
means that...
- He would have to change his password on each of the three computers
whenever he changed his password.
- If he kept his passwords different on each computer, then he would
have remember three passwords.
- Since a computer already had a "Tamara Jones" as the tjones user, Tom's
account on that machine is different from the other two.
Some argue that single sign-on is unsafe because the user only has one username
and password. But users are more likely to write down passwords, if
they have a lot of them or if they have multiple username/password combinations
on the network, and less likely to write down this information if it consolidated.
This goes double if network administrators are also enforcing "strong
password" policies.
Another angle on this problem is amount of operating systems and services
on the computer network.
Fig2 Various services/OSes using a centralized
account server
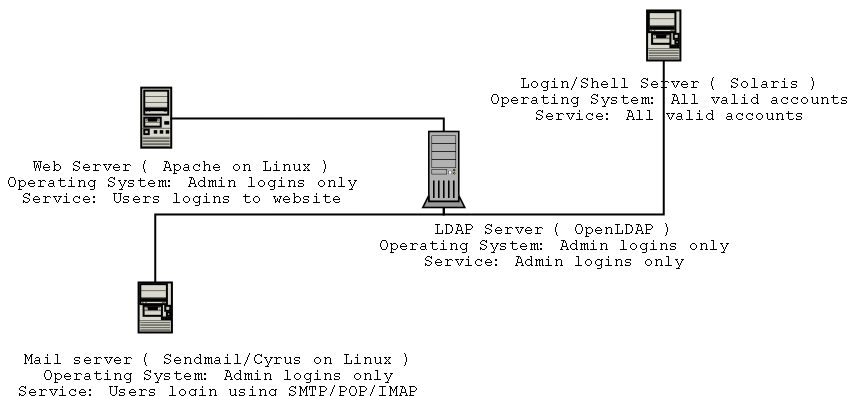
In this scenario, users are able to log into web-based applications on the
webserver running Apache webserver using their LDAP accounts/passwords, but
those same users are not allowed to log into the server using ssh, that is
restricted to administrator accounts only. This is archived by configuring
Apache to use LDAP as authentication module. This ability is buildt
into Apache 2 and comes as an extra module for apache 1. The mail server
uses Sendmail SMTP and Cyrus IMAP/POP servers for user account varification
also, and that to points to the LDAP server for accounts. The third
machine, the Login ( or shell ) server allows any user to login directly
to the server. It is configured to simply point to the LDAP server
for system accounts.
Without some sought of centralized server, every service would have a separate
password. That is, the user would have a "email password" and a "web
password", etc. Redunancy on the service level would be next to impossible
as well.

